SpyLoan Explained: How It Works, Its Impact in the Philippines, and How to Protect Yourself
Understanding SpyLoan: How It Works and Ways to Mitigate Its Risks
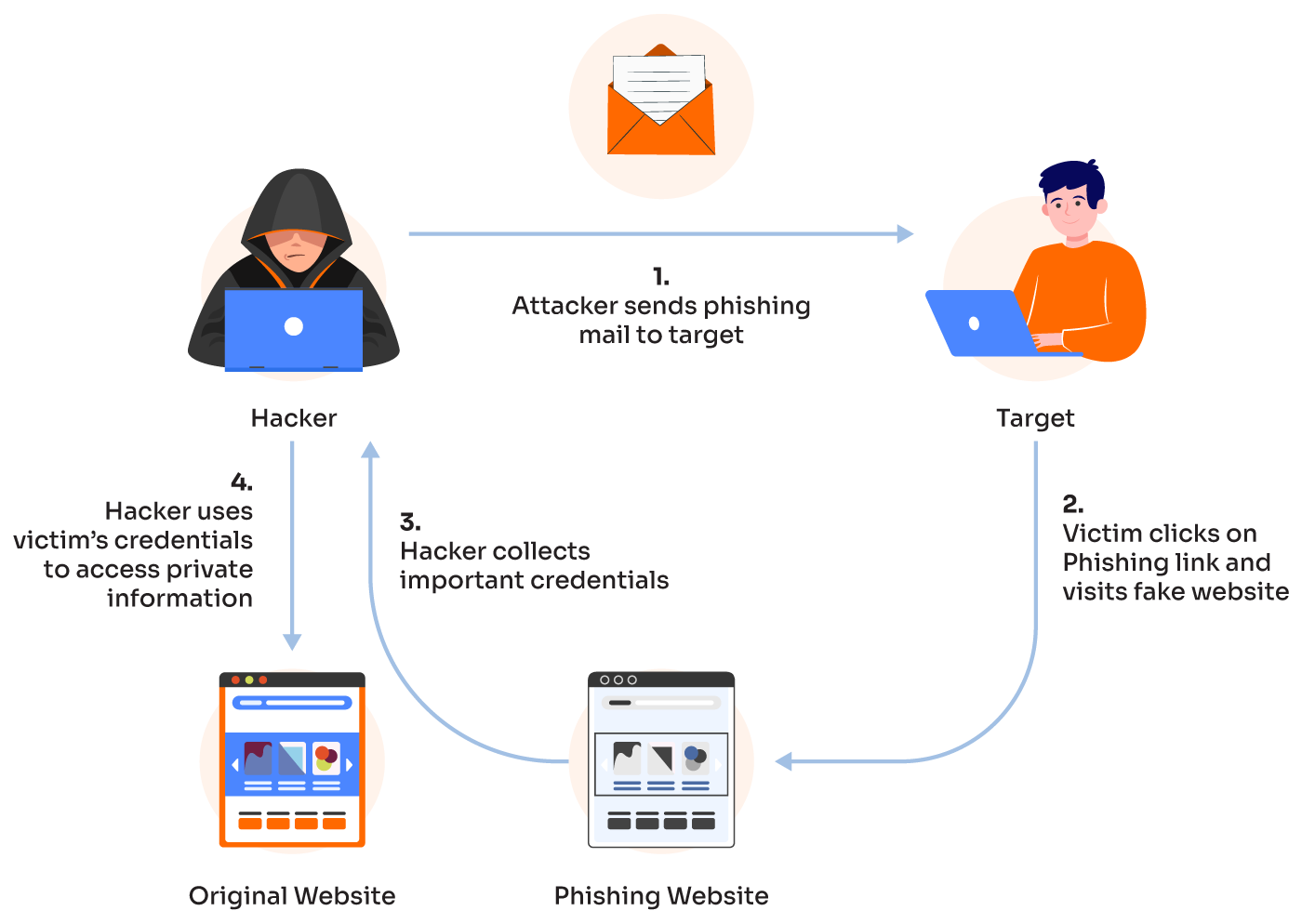
SpyLoan is a term used to describe a form of spyware commonly embedded within predatory lending apps. These apps typically target individuals in financial distress, often in countries with minimal regulation on digital financial services. SpyLoan applications gather sensitive data without user consent, leveraging this information to intimidate, harass, or blackmail borrowers.
How Does SpyLoan Work?
SpyLoan operates by embedding spyware functionalities within lending apps. Here’s how it typically works:
- Data Harvesting During Installation
Upon installation, SpyLoan apps request excessive permissions, such as access to contacts, SMS, call logs, photos, and location data. Many users, eager for quick loans, grant these permissions without fully understanding the implications. - Unethical Data Collection
Once granted access, these apps extract personal information, including:- Contacts: Used to harass borrowers or shame them by contacting their acquaintances.
- Messages and Call Logs: Exploited to monitor financial activities or gather more information about the user.
- Photos and Location: Used for blackmail or tracking.
- Harassment and Blackmail
Borrowers who fail to meet repayment deadlines are often harassed via calls or messages. Contacts in the borrower’s phone may also be notified, pressuring the borrower through public humiliation. - Unregulated Operations
These apps often operate in a gray legal area, exploiting loopholes in consumer protection laws and regulations in countries like the Philippines.
Are There SpyLoan Apps in the Philippines?
Yes, numerous cases have been reported in the Philippines where lending apps have engaged in unethical practices resembling SpyLoan behavior. In recent years, regulatory bodies such as the National Privacy Commission (NPC) and Bangko Sentral ng Pilipinas (BSP) have cracked down on such apps. However, due to the rapid proliferation of mobile applications, new apps often emerge to replace those that have been banned.
Some affected apps in the Philippines have been flagged for:
- Unauthorized access to personal data.
- Harassing borrowers by contacting their friends and family.
- Misusing sensitive data for extortion.
Example: The NPC investigated multiple online lending platforms, ordering the removal of apps proven to violate data privacy laws.
Mitigating the Risks of SpyLoan
To protect yourself from SpyLoan and similar threats, follow these guidelines:
1. Scrutinize App Permissions
- Before installing any financial app, check the permissions it requests. Legitimate apps should not require access to your contacts, photos, or location unless absolutely necessary.
2. Use Trusted Platforms
- Download apps only from official sources like Google Play or the Apple App Store. Avoid APK files from third-party websites.
3. Check Reviews and Ratings
- Read user reviews carefully. Look for complaints about data misuse or harassment.
4. Educate Yourself About Loan Providers
- Verify the legitimacy of the lending company. In the Philippines, check if the lender is registered with the Securities and Exchange Commission (SEC) and other relevant authorities.
5. Leverage Security Features
- Install mobile security apps to monitor app behavior and detect spyware.
6. Report Suspicious Apps
- If you encounter a SpyLoan app, report it to the NPC or SEC. This helps regulatory bodies act against predatory platforms.
7. Avoid Sharing Personal Data
- Be cautious about sharing sensitive data with online platforms. Even legitimate apps can become compromised.
What Should Authorities Do?
- Stronger Regulation
- Governments should enforce stricter data privacy laws, ensuring that all lending apps adhere to clear guidelines on data collection and usage.
- Consumer Awareness Campaigns
- Regularly educate citizens about the risks of SpyLoan and other digital threats.
- Proactive Monitoring
- Monitor app stores for malicious apps and remove them promptly.
- Strict Penalties
- Impose heavy penalties on companies that misuse user data or harass borrowers.
Final Thoughts
SpyLoan is a troubling manifestation of how technology can be misused to exploit vulnerable individuals. By staying vigilant, educating yourself, and reporting unethical practices, you can minimize the risks of falling victim to such predatory schemes. Moreover, with proactive measures from both users and authorities, the prevalence of SpyLoan apps can be significantly reduced, ensuring a safer digital financial landscape.